What is Pivoting?
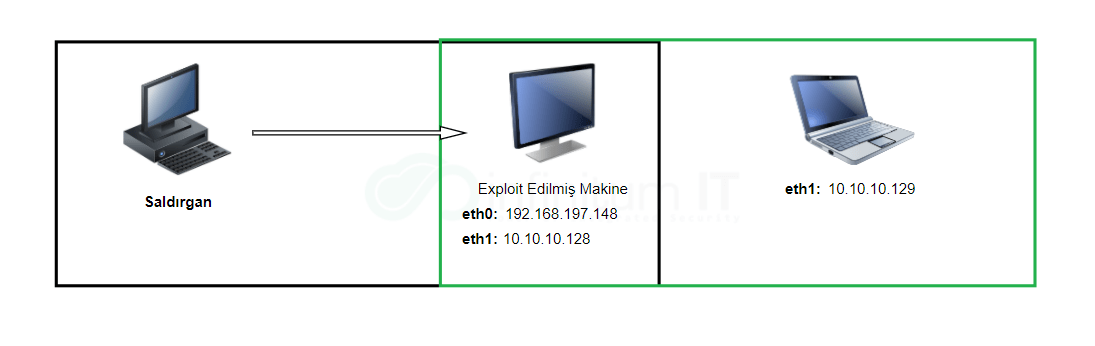
Pivoting (lateral movement) It is an important post-exploitation step. pivoting; Providing indirect access to hosts that cannot be accessed directly through other hosts/machines on the same network can be expressed as Thus, machines that do not have direct access become vulnerable to exploitation. If we look at this situation through an image, the subject can be better understood:
Machines in the green box in the image above eth1 is in the same network. The seized machine is also eth0 with another network. The attacker can directly access his system. eth1 unable to access your network 10.10.10.129 It will not be able to directly access the machine with the IP address. But at this point, the attacker; had previously taken 192.168.197.147 Access the machine with the IP address and then from here 10.10.10.129 It can gain access to its target by switching to the machine with the IP address, in other words pivoting can perform.
Concretizing all these stages through a step-by-step scenario will make the subject more understandable:
Post-Exploitation Stage in Lab Environment
According to the scenario, an attacker is located on the local network in the Active Directory environment. 192.168.197.148 It allows you to seize the machine with the IP address and obtain the login information and run the code remotely in the windows environment via metasploit. psexec that you do not have direct access to this machine by connecting to this machine 10.10.10.129 Suppose it is trying to reach the machine with the IP address.


After selecting psexec exploit over msfconsole in the steps in the screenshots above; RHOSTS as the IP address of the machine to be hijacked with 192.168.197.148, SMBDOMAIN domain associated with; SMBuser with username and SMBPass password is set with Target => 2 It is stated that the payload to be sent with the normal upload management will be sent. run The exploit was run with the command.

As can be seen from the above step, the payload has worked successfully and 192.168.197.148 A shell can be created on the machine with an IP address.
Action of Detecting and Pivoting Other Machines in the Network

As can be seen from the image above, the seized machine ipconfig When the command is entered, it is clearly seen that the machine is connected to two different networks. Here 10.10.10.0/24 over the hijacked machine as there is no direct access to its subnet. eth1 It is possible to switch to the working machine in the network. For this, the meterpreter autoroute captured with the help of script 192.168.197.148 It would be a good option to make a route over the machine with IP.

barley with the command on the eth1 network where there is no direct access. 10.10.10.129 The machine with IP is clearly visible.

Exiting the created shell with ctrl+c and returning to the meterpreter command screen again. run autoroute -s 10.10.100/24 By routing to the network specified with the command, run autoroute -p Active routing table can also be seen with the command.
Now 10.10.10.129 Access to the machine with IP is possible. With the help of Metasploit, you can test whether the operation is successful by performing a small port scan.

As can be seen from the last stage, the port scan has been successfully completed.