What is Cyber Threat Intelligence (CTI)?
Cyber Threat Intellingece (CTI) is to take necessary precautions by examining and analyzing the targets, purposes and behaviors of threat actors for organizations. Threat intelligence has become more important as organizations increase these threat actors. It is used for situations such as early detection and taking precautions against threatening situations with threat intelligence, and taking quick actions against threat attacks. In addition, cyber threat intelligence teams prepare reports about viruses, exploits and system vulnerabilities they find in the tools they use and share them around the world. In this way, they prevent attacks.
Data Sources of Cyber Threat Intelligence:
- Firewall, IDS, IPS and MDR tools
- System and log events
- Incident response outputs
- Gaining knowledge through social engineering
- Forums
- Following platforms created for cyber threat intelligence
Life Cycle of Cyber Threat Intelligence:
- Determination/Planning
At this stage, the situations that need to be protected from threat actors are determined first. For these situations, priorities are established for planning and measures to be taken. In the event of a data breach, the impact on the organization is planned.
- Collection
After the first stage, it is data collection in the cyber threat intelligence process. Here, the logs from the network and security devices are checked. At the same time, open source intelligence is done on platforms such as forums, social media, cyber intelligence reports, dark and deep web.
- Analysis
At this stage, an analysis is made using the data obtained. This data is made available.
- Spreading
After the analysis and examinations are made, these obtained situations should be shared with other teams within the institution. Information should be disseminated by informing the teams according to their needs.
- Feedback
After the dissemination phase, the decisions taken with the senior management and teams in the institution and the implementation of these decisions.
What Are the Benefits of Cyber Threat Intelligence?
- One of its biggest benefits is its ability to respond to incidents before an attack. For example, let's say a threat group in preparation for an attack has started to actively gather information and launch small-scale attacks. By researching this threat group, active-passive information collection processes can be made about them. In the event of a major attack, Cyber Threat teams have the opportunity to intervene in advance.
- According to my research, the amount of money spent by companies on false alerts is quite high. Cyber Intelligence teams can help companies a lot financially as long as they check for such false alerts. They can minimize the expenditures made.
- It prevents the detection of the data breach in an institution where a data breach is made and prevents the breach from being at an advanced level. They do a great job of detecting compromised systems from which devices in the enterprise with a data breach.
- As a result of their cyber-intelligence research, information is shared with other intelligence units, and security technologies are developed against cyber-attacks with these shares.
What is OpenCTI?
OpenCTI is a widely used open source cyber threat intelligence platform. The purpose of this platform is to see the contents and reports created by many analysts, such as zero-day threat actors, countries where threats and attacks are experienced, viruses, vulnerabilities, technical tactics and procedures used by attackers, IOC information about malicious software. Examples such as malware or attack events can also be accessed.
Setup
The following methods can be used to install the OpenCTI Platform. These;
- Deploy the VM template
- Use Docker (recommended)
- Install manually
- Use Terraform or Helm-Chart (Community version)
To access the OpenCTI Platform Demo; link
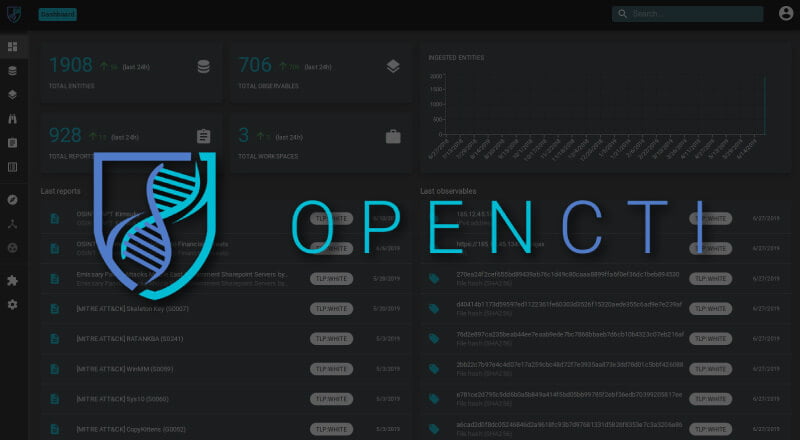
This is how the OpenCTI Platform dashboard appears when logged in.

- The Dashboard screen features Most popular tags, assets received, targeted countries, recent reports received, observable distributions and more.

- The analysis section includes reports, notes, opinions and external reference information from different sources.

- In this section, there are observable (type, value, labels etc.) states, artifact states, indicators (sigma, snort, ELK, Splunk etc.) and infrastructure information.

 Looking at the threats section, threat actors, intrusion sets (Technical, tactics and procedures, malware) are seen.
Looking at the threats section, threat actors, intrusion sets (Technical, tactics and procedures, malware) are seen.- The Arsenal content includes malware, attack patterns (TTPs), attack action cases, tools and vulnerabilities (CVEs).

- When we look at the assets title, sectors (such as clothing, agriculture), countries, cities, geographical locations, organizations, systems and individuals are seen.

- Another part, Data, performs functions such as data and data management (entities, relationships, background tasks, connectors, synchronization, data sharing) within OpenCTI.
Data Import
By entering the data import section in the upper right corner, the malicious file is uploaded to the OpenCTI platform.

Add Analysis

After entering the analysis section, pressing the plus icon at the bottom right starts the report adding process. In this section, we add the report using the name, publication date, type of report, description of the report, person or institution as the author (Microsoft, Kaspersky, Virustotal etc.), tags, flags (TLP) and external references parameters.
Events

- If we talk briefly about the events section, in this section, the places where the events are seen and the observed data can be accessed.
 Looking at the threats section, threat actors, intrusion sets (Technical, tactics and procedures, malware) are seen.
Looking at the threats section, threat actors, intrusion sets (Technical, tactics and procedures, malware) are seen.