Business Logic Weaknesses
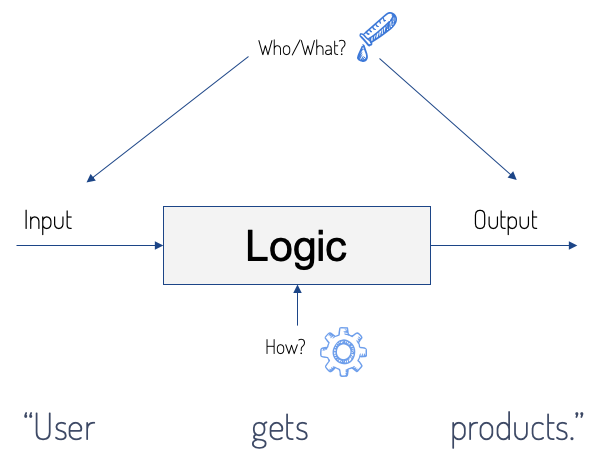
What is Business Logic? Business Logic is translated from English to Turkish as Business Logic. The rules for processing and interpreting the data of an existing application are called business logic. How Do Business Logic Vulnerabilities Occur? Business logic vulnerabilities, like most other vulnerabilities, occur when the data received from the user is not sufficient.