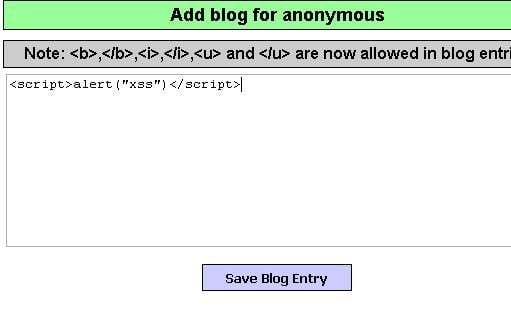
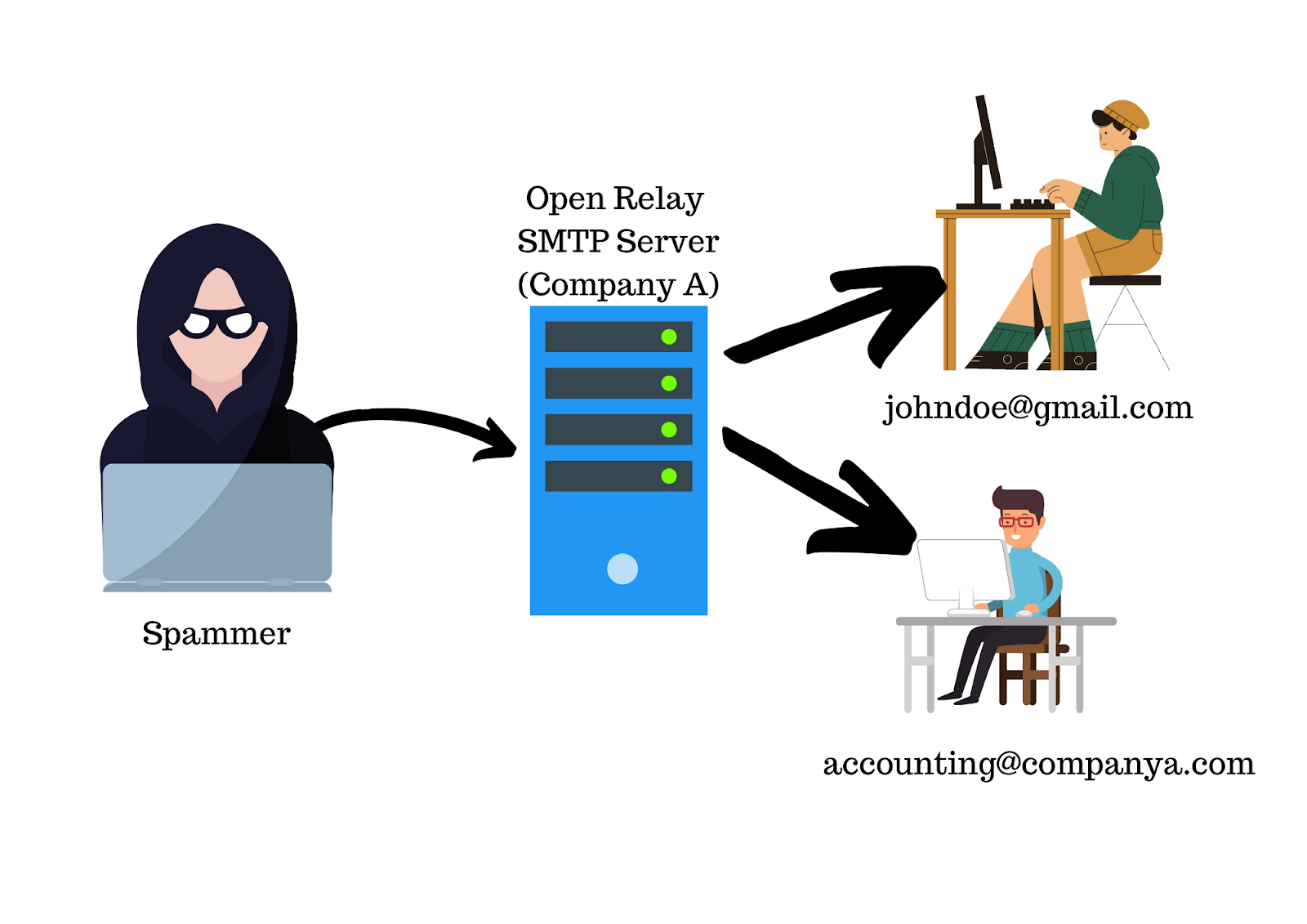
What is MALWARE?
Malware (malicious software) is a set of applications that slow down the computer or mobile device, cause the computer to crash and steal information. It also makes your computer part of a botnet. Computers in the botnet network can be used for DDoS attacks. to governments or through your computer.