Introduction
Windows is the most used Operating System in the world , especially when it comes to Enterprises . We use CTRL+ALT+DEL combination everyday, right ? We see lots of processes in Task Manager but how many of us know what these processes really do ? If you are a Blue Teamer in the Cyber Security field , you have to know the normal behavior of the core processes to detect unusual behaviors that may happen one day.
How to Detect Unusual Behaviors
Task Manager is a simple utility to check processes that your computer runs. You can open it by using CTRL+SHIFT+ESC combination. Click on “Details” tab.

Even though it seems a little bit complicated, it is not enough for us. We have to know parent and child process information, so we can use Process Hacker or Process Explorer tools instead of Task Manager.

So , as a Blue Teamer how do we detect an unusual behavior at someone’s computer in our company ? This is the place where EDR ( Endpoint Detection and Response) solutions come into play. But we will not go into EDR subject in this article.

Core Processes

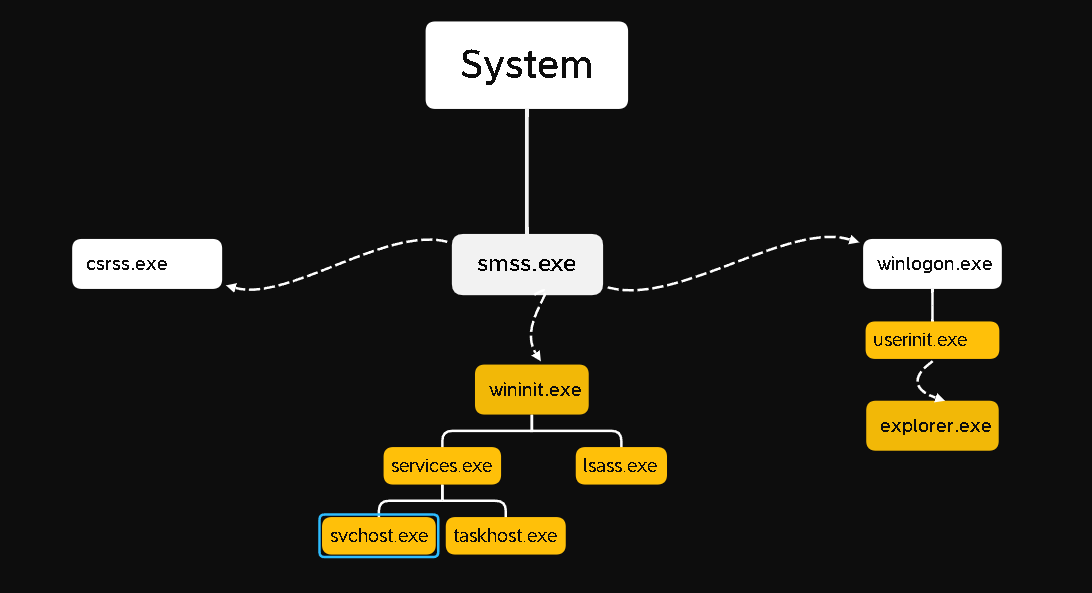
System Process
Our first process is System. Normally the PID’s (Process ID) are generated randomly. But the Process ID of System Process is always 4.
Path: C:\Windows\system32\ntoskrnl.exe
Parent: System Idle Process (0)
Number of Processes: One
Start Time: Boot
System Process > SMSS.EXE
Session Manager Subsystem is responsible for creating new sessions and environment variables , starting the kernel-mode and user-mode of the Windows subsystem.
Smss.exe starts csrss.exe and wininit.exe in an isolated Windows Session (Session 0) ,csrss.exe and winlogon.exe in user session (session 1).
Path: %SystemRoot%\System32\smss.exe
Parent : System
Number of Processes: One master and one child instance per session.
CSRSS.EXE
Client Server Runtime Process is user-mode side of the Windows subsystem. This process is always working and if something happens to csrss.exe all the system will crash. This process is responsible for Windows API available for other processes , Win32 Console Window , Process thread creation and deletion.
Path: %SystemRoot%\System32\csrss.exe
Parent: Created by an instance of smss.exe
Number of Processes: Many
WININIT.EXE
The Windows Initialization Process, wininit.exe, is responsible for launching services.exe (Service Control Manager), lsass.exe (Local Security Authority), and lsaiso.exe within Session 0.
Path: %SystemRoot%\System32\wininit.exe
Parent: Created by an instance of smss.exe
Number of Processes: One
WININIT.EXE > SERVICES.EXE
Service Control Manager (services.exe) handles system services; loading , interacting , starting/ending services etc. You can find information about these services in the registry , HKLM\SYSTEM\CurrentControlSet\Services.
Path: %SystemRoot%\System32\services.exe
Parent: wininit.exe
Number of Processes: One
WININIT.EXE > SERVICES.EXE > SVCHOST.EXE
The Service Host (svchost.exe) responsible for hosting and managing windows services. The services running in this process are DLLs. You can see these DLLs in the registry editor, HKLM\SYSTEM\CurrentControlSet\SERVICENAME\Parameters.
If you use Process Monitor you can see lots of svchost.exe. So it can be easy for a hacker to hide in it.
Path: %SystemRoot%\System32\svchost.exe
Parent: services.exe
Number of Processes: Many
LSASS.EXE
Local Security Authority Subsystem Service (lsass.exe) is a process for enforcing the security policy on the system. It verifies users when doing some tasks , like Cookies in browsers . Lsass.exe doing this job by creating security token for SAM , AD and NETLOGON.
This is another process adversaries target. Especially Mimikatz tool is trying to dump credentials from lsass.exe.
Path: %SystemRoot%\System32\lsass.exe
Parent: wininit.exe
Number of Processes: One
WINLOGON.EXE
The Windows Logon (winlogon.exe) is , as you can understand from its name, responsible for handling everything related to the user’s logon.
Path: %SystemRoot%\System32\winlogon.exe
Process: Created by an instance of smss.exe.
Number of Processes: One or more
EXPLORER.EXE
Windows Explorer (explorer.exe) gives the user access to their folders and files. I believe it is the most well-known process. It also provides functionality to other features such as Start Menu , Taskbar etc.
Path: %SystemRoot%\explorer.exe
Parent: Created by userinit.exe then exits
Number of Processes: One or more
Sources :
https://tryhackme.com/room/btwindowsinternals
https://nasbench.medium.com/windows-system-processes-an-overview-for-blue-teams-42fa7a617920